Just a collection of notes and screenshot that can help in getting ready for the RHCSA exam.
Basted on RHEL 7.
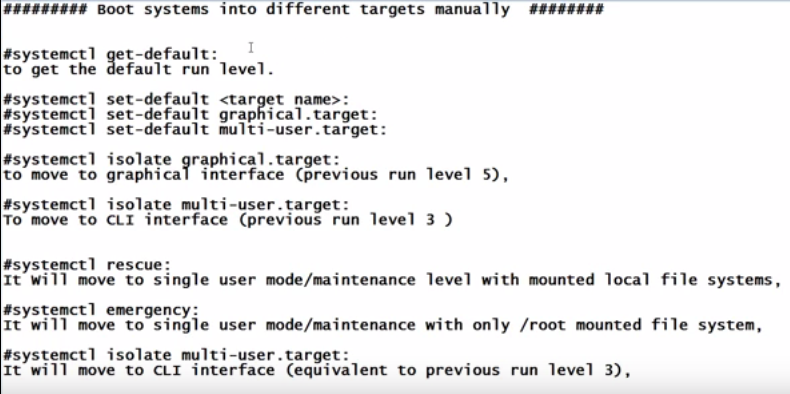
Boot systems into different targets manually
Configure networking and hostname resolution statically or dynamically
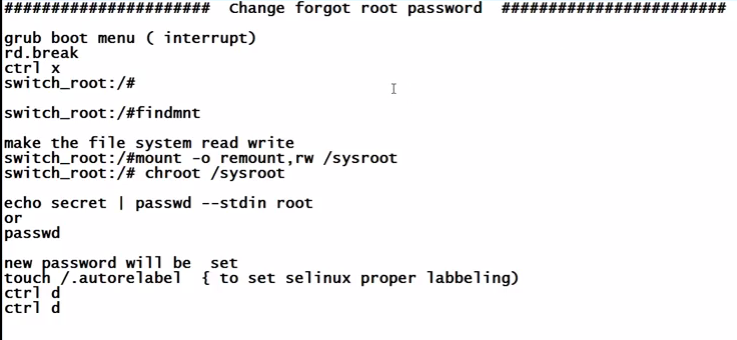
Interrupt the boot process in order to gain access to a system
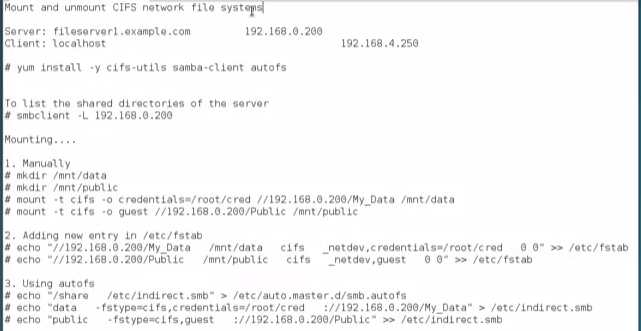
Mount and unmount CIFS network file systems
Configure a system to use time services
timedatectl timedatectl list timezones timedatectl set-timezone America/Phoenix timedatectl set-time 9:00:00 timedatectl set-ntp true/false timedatectl